2022 工大抗疫Wp
2022 工大抗疫Wp
选手:Pvr1sC
这比赛怎么基本都是原题,唯一的帮助可能就是学到点密码
Re
crackme
很简单,反编译
int __cdecl main(int argc, const char **argv, const char **envp) |
脚本
s = [0x66, 0x6D, 0x63, 0x64, 0x7F, 0x64, 0x32, 0x36, 0x6A, 0x6C, 0x3E, 0x3D, 0x39, 0x20, 0x6F, 0x3A, 0x20, 0x77, 0x3F, 0x27, 0x25, |
flag{a41be465-a50f-4124-b7ba-2766aff6baf2}
ez_py
运行文件,发现magic number error ,进行修改
修改一下文件内容
拿工具uncompyle6反编译
# uncompyle6 version 3.7.5.dev0 |
写脚本
from operator import le |
flag{da3c2a074cd3b7e5164cee34170832c8}
SuperFlat
有输出文件,感觉简单了
反编译发现基本都是mov,是movfuscator混淆
去mov混淆工具,好像没啥用。还是动调试试吧
大概看了一下,发现关键
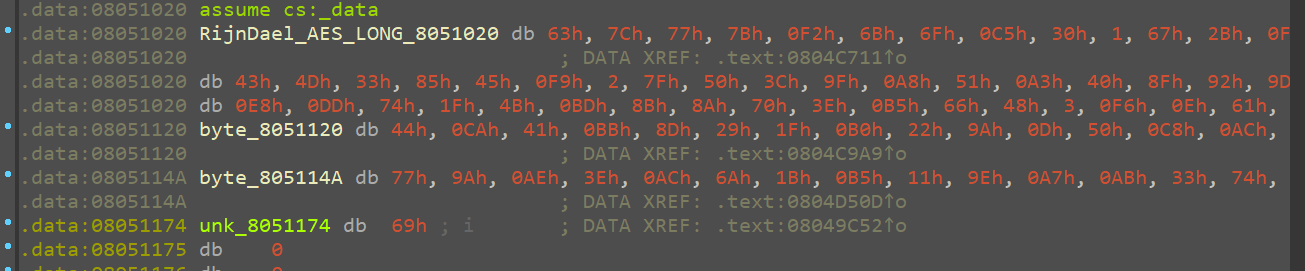
byte_805114A 和output文件内容一致,交叉引用进一步查看
经过分析伪代码如下
for i in range(42): |
sbox = [0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16] |
flag{d06f0bcc-93e0-9c5b-161e-e1464176d395}
pyc
拿网上工具跑
#!/usr/bin/env python |
明显不对,看来得改
将pyc改为机器码
import marshal |
将机器码手动改为
import hashlib |
看不出来啥的东西,找特征:
- 输入字符区间0~8 // len(a1) == 8 s.count(‘9’) == 0
- 输入长度72位 // len(s) == 72
- 9位一组,每组又分8次取索引对应值求和
- 每一组都要比前一组的值小
- 每次sum的和为唯一值 len(a2) == 1
看不出来没关系,
分析一下核心点sum究竟在做些什么,把a4运算的结果[l:l+3]打印出来,分析
# a4[1] ^ 64201746666225664 ^ 3446703994 = 64201748063452867
s = [6, 4, 2, 0, 1, 7, 4, 8, 0, 6, 3, 4, 5, 2, 8, 6, 7] |
输出:截取部分
[6, 4, 2]
[2, 0, 1]
[1, 7, 4]
[4, 8, 0]
[0, 6, 3]
[3, 4, 5]
[5, 2, 8]
[8, 6, 7]
[6, 4, 2]
len(a2) == 1然后根据这个特征是行列斜对角和都相等,然后有个专门的名称,“三阶幻方”,开始以为是数独
把结果都写出来,整体值-1排序拼接,从大到小
723048561
705246381
561048723
507642183
381246705
327840165
183642507
165840327
把上面的数字拼接起来然后md5就是flag
723048561705246381561048723507642183381246705327840165183642507165840327
misc
签到题
flag{study_hard_and_make_progress_every_day}
你悟了吗
先天八卦数:乾(1)、兑(2)、离(3)、震(4)、巽(5)、坎(6)、艮(7)、坤(8)
后天八卦数:乾(6)、坎(1)、艮(8)、震(3)、巽(4)、离(9)、坤(2)、兑(7)
替换成数字 ,用先天卦
脚本
|
miao
用steghide提取隐藏文件,(这实属想不到,工具试出来的)
$.\steghide.exe info C:\Users\86177\Desktop\CTF\工大抗疫\Misc\miao\miao.wav |
flag{0f83ca08-c51c-4574-b2cd-bbdd786ae807}
brokenpassword
使用字典爆破,密码 american
解压出flag
flag{5BAF2AB2-3C15-4B6D-9BC4-51BCC27B718E}
i_am_scriptkids
base解密
分别有16 32 64 85
手动解一下,三十次
import base64 |
得到
flag{90672c52-200d-11ec-bdc8-33c511816e47}
qrcode
拼图,拼了半小时,555,然后扫码就出了,没什么好说的
flag{b9f32f7f-f30c-408f-b0bd-64c03a60e915}
Crypto
simpleCrypto
维基尼亚密码
There are moments in life when you miss someone so much that you just want to pick them from your dreams and hug them for real! Dream what you want to dream;go where you want to go;be what you want to be,because you have only one life and one chance to do all the things you want to do;key is zheshimima |
解压密码zheshimima,解压出flag
flag{5a851c56-75a3-4899-911b-0bb48bc31a52}
ezrsa
分解n
fac: factoring 60451215053202473004940952621742735161658776366659855277231745089406139921920247699935855664424690715827311751776376765039253720695107034417349327247413785321282310515940197744035889015386751355695663945883766755254889478550954910913617031495509031272479126330010210073745554866695555903062215643355046569531 |
中国剩余定律
低加密指数广播攻击
import gmpy2 |
Crypto1
from libnum import n2s, s2n |
flag{8ac9f9e3-82ba-ff7e-ac7b-235a02d891ef}
Crypto2
import libnum |
flag{afb1e6f2-9acb-efde-ad7c-246a99d8f1fd}
Web
web1
抓包发
client-ip: 127.0.0.1
flag{ed59cf0f-c1e1-49e1-abea-8309f67647ab}
web2
点击访问该首页,发现存在 ?url 跳转网址
访问flag.php发现要ping命令执行,但需要本地访问,试了X-Forwarded-For 还有client-ip: 127.0.0.1都不能,
想起来上面的URL任意访问
然后是多条命令执行用;隔开
http://eci-2ze1odj66lcxjp6jkpj6.cloudeci1.ichunqiu.com/?url=127.0.0.1/flag.php?cmd=1;ls
flag.php flag_is_here.php index.php
查看flag_is_here.php 发现flag
flag{70a3b5fc-2f50-418f-9c1d-af7f25c347ca}